Now that we have the base WebVPN/Anyconnect set up and configured with a certificate I think its pertinent to discuss some of the fundamentals. I hope you found the configuration up to this point fairly easy. I find that CLI configuration is far less complicated/convoluted than using the ADSM. However it should be noted at this point that since 8.2 code rolled out there are some items we HAVE to use the ASDM for. We’ll get to those later. So lets discuss some of the core parts of a VPN configuration on a ASA. Once we understand those we’ll talk about some other configuration features specific to WebVPN and Anyconnect.
There are a couple main parts of any client VPN configuration on an ASA. Two of the core configuration components are tunnel groups and group policies (crypto maps are a key part of IPSec based L2L and Client VPN’s but aren’t relevant with SSL VPN so I wont be discussing them at this point).
Tunnel Groups
I like to think of tunnel groups as the core of a VPN configuration. Tunnel Groups have two main elements which are Attributes and Types. It helps to visualize these in a hierarchy.
Types
ipsec-l2l – L2L Configurations
ipsec-ra – The old IPSec Client VPN type (Deprecated)
remote-access – The new Client VPN type for both SSL and IPsec
webvpn – The old SSL Client VPN type (Deprecated)
Attribute Sets
general-attributes – General Attributes used with most tunnel group configurations
ipsec-attributes – Specific IPSec Attributes used for L2L and Client IPSec configurations
ppp-attributes – Specific PPP (Point to Point Protocol) attributes
webvpn-attributes – Specific SSL Attributes used for WebVPN configurations
So hopefully looking at it like this, you can discern a couple of things. For instance, if we are doing a L2L VPN configuration we’ll configure the type as ‘ipsec-l2l’ and define attributes within the ‘ipsec-attributes’ set. If we were configuring WebVPN, our type would be ‘remote-access’ and we would define ‘webvpn-attributes’. Make sense? On top of that we usually define ‘general-attributes’ with client VPN configuration since you define your DHCP scope underneath that attribute type.
Additionally, tunnel groups would be where we would define authentication. By default the ASA assumes we want to use Local authentication. Since we didn’t specify a different authentication group in our WebVPN setup, it defaults to Local authentication. There isn’t any need to define authentication in the tunnel group unless you are configuring Radius or some other type of user authentication.
One distinction I like to make clear is that if we are using just the WebVPN portal we don’t use any group policies. If you noticed when we configured our SSL VPN we specified a group policy defining a DNS server, a split tunnel ACL, and our DNS domain name. None of that is relevant in the WebVPN portal. Those are all configuration options for VPN that get pushed to the client in what we call “mode config”. These are options that the client uses in its VPN Network config. That being said, even though we defined a DNS server in our group policy it won’t be used in the portal. To use DNS resolution in the portal (We’ll get into why you would want to in a later post) we need to define one in the tunnel group. You’ll notice that if you go under a “Connection Profile” (Tunnel Group) in the ASDM there is a section that asks for a DNS server. If you don’t have one defined it will give you a warning as shown below. 
What’s interesting about this is that once you define a DNS server in a tunnel group, its used for all of your tunnel groups. Look at what happens in the ASDM after I define a DNS server in one of my tunnel groups.
It uses the server you define for all of your tunnel groups. Really I think this should be an option under ‘Device Setup’ right underneath ‘Domain Name’. You’ll notice that if you change the domain name in the tunnel group the domain name of the device changes and vice versa. I’m not sure why they give you the option to set a DNS server in each tunnel group, I think its just more confusing. The CLI clears this up pretty well by listing the DNS server and the domain name in a server group. Here’s what the CLI config looks like for both the DNS server and domain name.
dns server-group DefaultDNS
name-server 10.10.10.10
domain-name domain.com
Isn’t that just easier to understand? You have one domain name and one global DNS server for the entire device. I think it just makes more sense than what the ASDM displays.
Again, I’ll point out another reason why the ASDM is more confusing. In the ASDM they refer to tunnel groups as “Connection Profiles”. On top of which there are three different places to select them in the VPN configuration screen all of which provide you with different configuration options. Try it out yourself, when you click on any one of these you get a different configuration window on the right. Just another reason to use the CLI.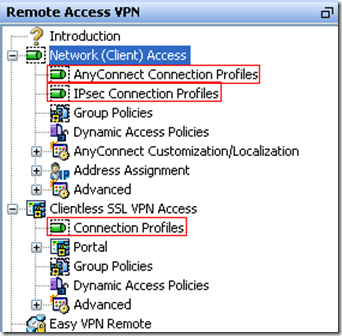
Summary – Tunnel groups are what I consider the base of VPN configuration. They are very easy to configure in the CLI. You simply define a tunnel group by giving it a name and a type and then you add attributes to it based on what sort of VPN you are configuring (L2L or remote-access).
Group Policies
Now that you have a tunnel group defined, you can associate group policies with it. Group policies are where you define options for the Anyconnect client to use such as DNS Server, domain name, and split tunnel ACL’s. Keep in mind that group policies are defined almost identically for Anyconnect and IPSec client VPN.
The group policy is where you define a lot of the options and policies that directly affect the user’s VPN experience. Before we start playing with the group policy settings we need to understand exactly how and why they are applied. Group policy on the ASA relies on what Cisco calls inheritance. There is one default group policy (DfltGrpPolicy(System Default)) on the ASA right from the start. When you create a new group it automatically inherits all of the settings from the default group policy. As I begin to specify settings for a particular (non-default) group policy, the inheritance is replaced with the value that I configure. So if you create a new group policy and check its properties in ASDM you’ll see that all of its properties are set to inherit. A good example of using inheritance would be configuring your internal DNS server in the default policy. In most cases that server won’t change regardless of who is connecting. When you set it in the default policy (and you don’t configure one in the specific policy) you don’t need to specify one in any other policies, it will just inherit from the default policy by default.
Just to beat the dead horse about the ASDM being confusing one last time. In the ASDM there are yet again two places to look at group policy settings. On first glance when you click between the two group policy icons on the left hand side of the screen the properties appear to be the same on the right. Once you click the ‘Edit’ button you’ll notice that there are different options under each icon. Confusing and weird (in my opinion)….
Summary – There are a lot of features that can be configured in group policies. I’m not even go to try to get into them during this post. My objective here was to give you a brief description of group policies and tunnel groups. Hopefully now you have a better understanding of how they interact with each other and as a whole are part of the Anyconnect and WebVPN solutions. In the next post we are actually going to talk about portal customizations and how they relate to group policies and tunnel groups.

Clear and exlicit. What a great read.
still valid ! good job!
helped me – Thankyou!
Super! Thanks. I was struggling with how these fit together.