Probably one of the larger items I have been getting config requests for is wireless configuration, specifically Guest and Production wireless SSID’s. That is to have an AP (Cisco!) that can host dual SSIDs. The Prod network can get everywhere and the Guest network can only get out to the internet. The thing about the base license ASA’s is that the DMZ can only go one way. That is it can’t be a real DMZ and connect back to you internal network as well. This makes it pretty useful as an interface for the guest network. Also, this doesn’t have to be just for wireless. Now that you have that VLAN you can tag it on some other access ports in your conference room for guests to use. Just keep in mind that you’ll probably have to deal with some unhappy users who can’t get to their power point stored on the server from time to time.
Notes
-Insert your relevant information between <>
-Console prompts are show in green
-Text in blue are variable names I made up, feel free to change them
Pre Reqs
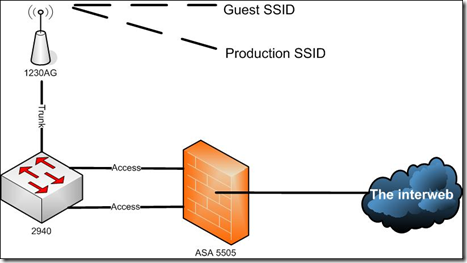
-A Cisco AP that can host dual SSID’s and is configured to do so (I used a 1230AG)
-A Layer 2 switch that can do trunking (I used a 2940) The non-Sec+ 5505’s don’t have the ability to trunk. So we need to use a managed switch and plug the AP into a trunk port (So it can see more than 1 VLAN) and then tag two access ports on the switch which connect to two corresponding access ports on the ASA one in each VLAN.
-A Cisco ASA that’s in production and has the 3rd interface available. By production I mean it has NAT/PAT setup correctly and is a functioning firewall.
Configure a third VLAN (vlan 3)
ASA(config)# int vlan 3
ASA(config-if)# no forward interface Vlan1
ASA(config-if)# nameif GUEST
ASA(config-if)# security-level 50
ASA(config-if)# ip address <ip address> <subnet mask>
Assign the VLAN to a switchport
ASA(config)# int ethernet0/<Interface number>
ASA(config-if)# switchport access vlan 3
Create a new DHCP scope for the guests and apply it to the VLAN
ASA(config)# dhcpd address <start address>-<end address> GUEST
ASA(config)# dhcpd dns <Outside DNS server> interface GUEST
ASA(config)# dhcpd enable GUEST
Enable outbound access by adding to the NAT
ASA(config)# nat (GUEST) 1 <Guest subnet number> <Guest subnet mask>
Configure the Managed switch you are using to connect the AP and the ASA
Configure a port on the switch for the AP
Switch(config)# int ethernet0/<Interface number>
Switch(config-if)# switchport mode trunk
Switch(config-if)# switchport trunk allowed vlan <production vlan number>, 3
Configure a port on the switch for the Guest VLAN
Switch(config)# int ethernet0/<Interface number>
Switch(config-if)# switchport access vlan 3
Configure a port on the switch for the Production VLAN
Switch(config)# int ethernet0/<Interface number>
Switch(config-if)# switchport access vlan <production vlan number>
Cabling
The cabling is pretty easy. Plug a patch cable between the AP and the port you tagged as a trunk on the switch. Then plug two more patch cables into the switch. One in the port you configured for VLAN 3 and the other into the port you configured for your production VLAN. Then simply plug the other end of those cables into the ASA in the corresponding port per your VLAN configuration. We are essentially doing the work of a trunk port with physical cabling. Each cable is carrying traffic for a specific VLAN between the two devices. If we had a Sec+ license on the ASA we could take the switch out of the picture and tag the port on the ASA as a trunk. This would allow it to carry both VLANs over the same cable. Additionally with the Sec+ we could use the built-in POE on the ASA 5505 models to power the AP.
Conclusion
It’s not that hard to configure and setup, the catch is you’ll need a L2 switch if you don’t have a Sec+ license.

This looks like it’s gonna save me from plopping down some cash on a Sec+ license…. I owe you a beer. 🙂
Thanks for reading!
Yeah, I thought I might have to buy one as well. Then after thinking about it for awhile I realized that the interfaces on the ASA werent any different than a switch and I could do the trunking anywhere.
Hope it works out for you.
Thanks – jon
This didn’t work for me:
ASA(config)# nat (GUEST) 1
Changed to this:
ASA(config)# nat (GUEST) 1 0.0.0.0 0.0.0.0
Not sure the difference here, but it didn’t work when using the subnet and mask as suggested.
Brackets trunicated my message… should have read:
This didn’t work for me:
ASA(config)# nat (GUEST) 1 (Guest subnet number) (Guest subnet mask)
That’s interesting. What does a ‘show run nat’ show you? I guess technically since you specify (GUEST) it would still work since you are just talking about NAT’ing any traffic on the guest interface out. The commands probably have the same effect. What error did you get when you tried specifying the subnet number and mask in the NAT statement? Or did it just not work at all?
It just didn’t work.
Here’s what show run nat displays:
nat (inside) 0 access-list nonat
nat (inside) 1 0.0.0.0 0.0.0.0
nat (GUEST) 1 0.0.0.0 0.0.0.0
Thanks a bunch, all working now, although it was a chore for a relative Cisco newb. 🙂
Hey guys
I am using kind of a diffrent senario were the AP will be connected directly to the switchport of the asa. I know that prior to 8.0 the asa did not support the native vlan feature since I woulkd like to create 2 ssids one for coorporate access and one for guess. My question is how I need to configure my asa to support that configuration ?
Hi there. Well first off, does your ASA support trunking? The AP will need to be a trunk port to support more than one VLAN. Since you want two SSIDs, you’ll want two VLANs going to the AP. Lets start there.
Yes I agree I think these asa’s(5505) came with the base licence so I would need to upgrade to the advanced security licence that supports trunking and up to 20 vlans I believe. I have seen mixed answers so I am not sure if I would still need to put a switch in between ( my guess in no) if my asa supports trunking. My deployment would be very similar to what you have presented on your solution but eliminating the switch.
Can you drop a how to for a sec plus firewall. Or tell me which parts I can subtract from the how to get my asa and ap541n going. Thanks
It there anyway to send me a how to with a asa 5505 sec plus with a ap514n. Or show me which parts I subtract from this tutorial to get it going. Thanks
Edwin
Sorry about the double post. I got back to the site and my post wasn’t there. 🙂
Im confused about your question. With a Sec+ license you can use the same config. If you don’t want to use the switch, you should be able to configure the trunk on the ASA itself.
Im not familiar with that AP. Does it support bridge interfaces (BVI)? VLAN per SSID?
So configuring with the switch and using vlans, does my switch need to be a L3 or an L2 switch?
Do the VLANs need to be Tagged?
I appreciate any feedback, I know this article has been out here a long time.
Yep – you’re just trunking VLANs so layer 2.
Pingback: RSPAN,SPAN and Mirror ports – skminhaj
Hello,
Is this post still available for comments? I would like to ask yoou a question about my setup. Can you PM me, possibly
Pingback: How to properly add guest essid to cisco AP and asa5505 - Boot Panic